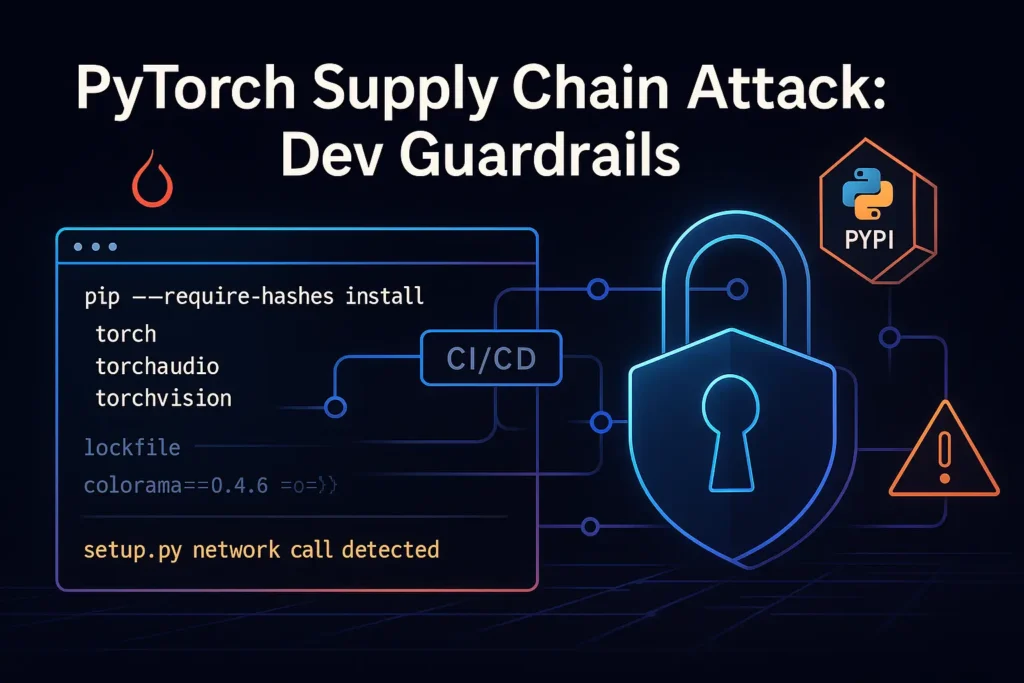
7 Proven Supply-Chain CI Hardening Wins (2026)
7 Proven Supply-Chain CI Hardening Wins (2026) Modern attackers don’t need to break your production firewall if they can poison what you ship. In 2026, Supply-Chain CI Hardening is how engineering teams prove build integrity, reduce dependency risk, and stop “small” pipeline shortcuts from turning into incident-level compromises. This guide is dev-first and copy/paste-heavy. We’ll […]