OPA vs Cedar: 7 Proven Steps to Ship Policy-as-Code
Why this matters now
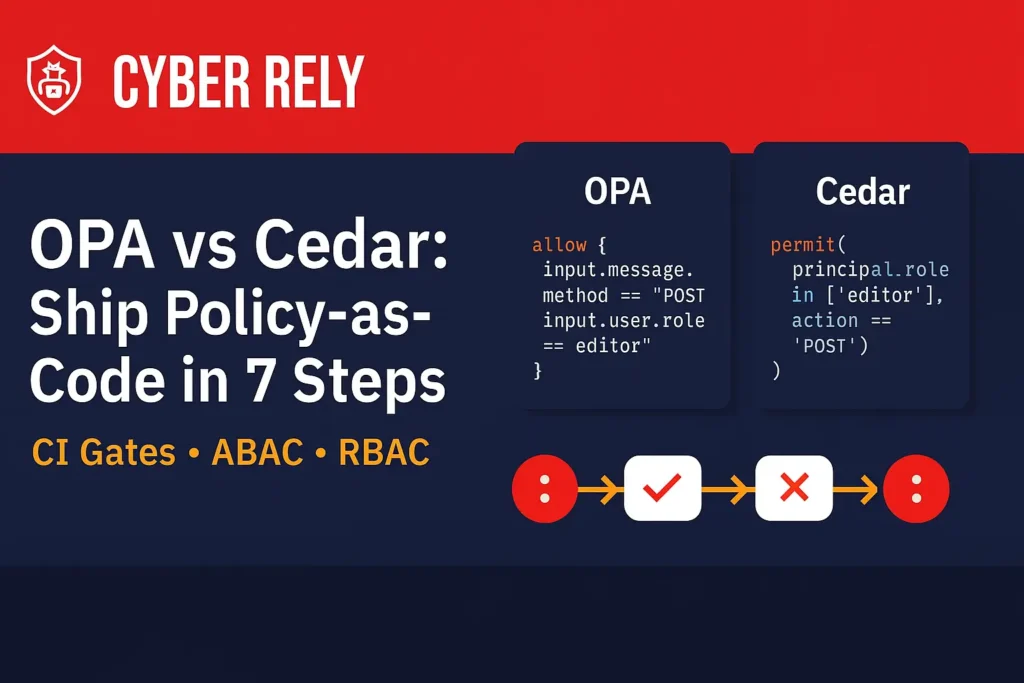
Modern apps need authorization that’s testable, reviewable, and observable. Two strong options are OPA (Open Policy Agent) with Rego and Cedar (policy language + embeddable engine). Below is a practical, code-heavy guide to help developers and engineering leaders choose wisely and ship policy-as-code with CI gates—without slowing delivery.
Want merge-blocking checks in CI/CD? See CI Gates for API Security: OPA Rules You Can Ship → https://www.cybersrely.com/ci-gates-for-api-security/
🔗 Need hands-on help? Book a quick assessment via our partner services at Pentest Testing Corp — Risk Assessment and Remediation.
1) OPA vs Cedar: When to choose which
| Dimension | OPA (Rego) | Cedar |
|---|---|---|
| Model fit | General-purpose policies; great with K8s/Envoy/Cloud Native | Fine-grained authz with principals/actions/resources; strong ABAC/RBAC |
| Runtime shape | Sidecar (Envoy ext_authz), daemon, or library | Primarily in-process library (very low latency); can be wrapped as a local service |
| Latency/footprint | In-memory eval is fast (<1–2 ms typical); sidecar adds ~network hop | In-process eval typically sub-millisecond; tiny footprint |
| Tooling | Conftest, Bundles, partial eval, decision logs, Gatekeeper | Schemas, policies, templates; SDKs; policy validation and tests |
| Best for | Platform policy, K8s admission, API gateways, multi-language estates | App-level authz in services where consistency & perf are critical |
| Policy language | Rego (Datalog-style) | Cedar (resource-centric with schema) |
Rule of thumb: If you already run Envoy/K8s and want a unified policy plane, OPA is ergonomic. If you need ultra-low latency, in-process checks with a clear principal-action-resource schema, Cedar shines.
2) Deployment patterns that scale (sidecar vs library vs gateway)
A. Sidecar (OPA + Envoy ext_authz)
Good when you want language-agnostic enforcement at the edge or per-service.
Kubernetes Deployment (excerpt):
apiVersion: apps/v1
kind: Deployment
metadata:
name: orders
spec:
template:
spec:
containers:
- name: app
image: ghcr.io/example/orders:latest
ports: [{containerPort: 8080}]
env:
- name: AUTHZ_ADDR
value: "http://127.0.0.1:8181"
- name: envoy
image: envoyproxy/envoy:v1.29.0
args: ["-c", "/etc/envoy/envoy.yaml"]
ports: [{containerPort: 8443}]
volumeMounts:
- { name: envoy-config, mountPath: /etc/envoy }
- name: opa
image: openpolicyagent/opa:latest-envoy
args:
- "run"
- "--server"
- "--addr=localhost:8181"
- "--set=plugins.envoy_ext_authz_grpc.addr=:9191"
- "--set=decision_logs.console=true"
ports: [{containerPort: 8181}, {containerPort: 9191}]
volumes:
- name: envoy-config
configMap: { name: envoy-config }Envoy ext_authz filter (snippet):
http_filters:
- name: envoy.filters.http.ext_authz
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.http.ext_authz.v3.ExtAuthz
transport_api_version: V3
grpc_service:
envoy_grpc: { cluster_name: opa_ext_authz }
include_peer_certificate: falseB. Library (Cedar in-process)
Tight latency budgets and local context? Embed Cedar directly in your service (example in Rust):
use cedar_policy::*;
fn allow(request: Request, policy: &PolicySet, entities: &EntityStore) -> bool {
let res = authorize(&request, policy, entities, None);
res.decision() == Decision::Allow
}C. Gateway (OPA at API gateway)
Centralize checks at ingress; useful for REST/GraphQL without touching every service. Combine with service-level checks for defense-in-depth.
3) Authoring policies: ABAC/RBAC for REST, gRPC, GraphQL
OPA / Rego — hybrid RBAC + ABAC
Input (from Envoy): method, path, user claims, resource, action.
package httpapi.authz
default allow = false
# Basic RBAC
role_bindings := {
"alice": ["admin"],
"bob": ["support"]
}
role_perms := {
"admin": [{"action": "write", "resource": "orders:*"},
{"action": "read", "resource": "orders:*"}],
"support": [{"action": "read", "resource": "orders:*"}]
}
# ABAC condition: region must match
region_match {
input.user.region == input.resource.region
}
# Resource match helper
resource_matches(pattern, res) {
startswith(res, trim(pattern, "*"))
}
allow {
user := input.user.name
some role
role := role_bindings[user][_]
some p
p := role_perms[role][_]
p.action == input.action
resource_matches(p.resource, sprintf("%s:%s", [input.resource.type, input.resource.id]))
region_match
}Evaluate via OPA HTTP API:
curl -s localhost:8181/v1/data/httpapi/authz/allow -d @- <<'JSON'
{
"input": {
"action": "read",
"user": {"name":"bob","region":"eu-west-1"},
"resource": {"type":"orders","id":"123","region":"eu-west-1"}
}
}
JSONCedar — schema + policies
Schema (entities + actions):
entity User {}
entity Order {
attributes { region: String }
}
action ReadOrder appliesTo (principal, resource) when { principal is User, resource is Order };
action WriteOrder appliesTo (principal, resource) when { principal is User, resource is Order };RBAC binding as entities:
{
"uid": "User::\"bob\"",
"attrs": { "region": "eu-west-1", "roles": ["support"] },
"parents": []
}Policy: allow read if role has read AND ABAC region rule
permit(
principal,
action in [ReadOrder],
resource
)
when {
"support" in principal.roles && principal.region == resource.region
};Request evaluation (JSON-ish):
{
"principal": "User::\"bob\"",
"action": "ReadOrder",
"resource": {
"__entity": "Order::\"123\"",
"region": "eu-west-1"
}
}4) Wiring REST, gRPC, and GraphQL
REST (Node/Express) → OPA sidecar
import fetch from "node-fetch";
export async function authz(req, res, next) {
const decision = await fetch("http://127.0.0.1:8181/v1/data/httpapi/authz/allow", {
method: "POST",
headers: {"Content-Type":"application/json"},
body: JSON.stringify({
input: {
action: req.method === "GET" ? "read" : "write",
user: req.user, // set by upstream authn
resource: { type: "orders", id: req.params.id, region: req.user.region }
}
})
}).then(r => r.json());
if (decision.result === true) return next();
res.status(403).json({error:"forbidden"});
}gRPC (Go interceptor) → OPA sidecar
func AuthzUnaryInterceptor(next grpc.UnaryHandler) grpc.UnaryHandler {
return func(ctx context.Context, req interface{}) (interface{}, error) {
input := map[string]interface{}{
"action": "write",
"user": ctx.Value(UserKey{}),
"resource": map[string]interface{}{"type":"orders","id":"123","region":"eu-west-1"},
}
allowed, err := queryOPA(ctx, input) // http POST -> /v1/data/httpapi/authz/allow
if err != nil { return nil, status.Error(codes.Internal, "authz error") }
if !allowed { return nil, status.Error(codes.PermissionDenied, "forbidden") }
return next(ctx, req)
}
}GraphQL (Apollo) directive → Cedar in-process
const isAllowed = (principal, action, resource) =>
cedar.authorize({ principal, action, resource }).decision === "Allow";
const resolvers = {
Query: {
order: async (_, { id }, ctx) => {
const resource = { __entity: `Order::"${id}"`, region: await regionOf(id) };
if (!isAllowed(`User::"${ctx.user.id}"`, "ReadOrder", resource)) throw new Error("Forbidden");
return loadOrder(id);
}
}
}5) CI gates: block merges on failing authz checks
Rego tests with Conftest (GitHub Actions)
name: policy-checks
on: [pull_request]
jobs:
rego-tests:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Run Rego unit tests
run: opa test policies/*.rego
- name: Validate manifests/contracts
run: |
conftest test k8s/ --policy policies/
conftest test api/openapi.yaml --policy policies/Cedar policy/unit tests (custom script)
#!/usr/bin/env bash
set -euo pipefail
for t in tests/*.json; do
echo "Running $t"
cedar-eval --policies cedar/policies/ --schema cedar/schema/ --request "$t" | \
jq -e '.decision=="Allow"' > /dev/null
doneGate merges if tests or
cedar-evalchecks fail. Add required checks in your repo rules.
6) Observability: decision logs, metrics, and drift
OPA decision logs (ship to your logs/OTel)
{
"labels": {"service":"orders","version":"2025.11.1"},
"decision_id":"6f6f-...",
"path":"/httpapi/authz/allow",
"input":{"action":"read","user":{"name":"bob","region":"eu-west-1"}},
"result":true,
"metrics":{"timer_rego_query_ns":380000}
}Quick wins
- Emit policy version and bundle SHA in every decision log.
- Export counters:
authz_allow_total,authz_deny_total,authz_error_total, and latency histograms. - Alert on drift (runtime policy SHA ≠ main branch SHA).
Cedar in-process
- Wrap
authorizeto logprincipal/action/resource, decision, policy set version, and timing. - Expose
/metricsin your service; scrape with Prometheus.
7) Gradual rollout & rollback guardrails
- Shadow mode: evaluate decisions but don’t enforce; compare with app logic.
- 10%→50%→100% traffic: turn on enforcement behind a feature flag.
- Fail-closed for Denies; fail-open for Errors only during early phases, then converge to fail-closed.
- Version pins: OPA bundles via digest; Cedar policy set versioned in lockfiles.
- Instant rollback: keep N-1 policy bundle and feature flag to revert in minutes.
End-to-end “real-time” quickstart (you can copy-paste)
- Model your world (users/resources/actions).
- Pick runtime: OPA sidecar (Envoy) or Cedar library.
- Write policies (Rego/Cedar) with unit tests.
- Wire app (REST/gRPC/GraphQL) using snippets above.
- Add CI gates (Rego tests, Cedar eval).
- Turn on logs & metrics; alert on drift.
- Roll out gradually with clear rollback.
Performance notes & tips
- Keep inputs small; pass only what the policy needs.
- Prefer in-process where tail latency is critical (Cedar), or sidecar when you want a common control point (OPA).
- Use partial evaluation (OPA) or pre-compiled policies (both) for hot paths.
- Cache subject → entitlements for read-heavy APIs; invalidate on role/attr change.
Security hardening checklist
- Schema everything (Cedar schema, input contracts for OPA).
- Least privilege defaults; explicit denies for sensitive actions.
- Request-scoped context only; never pull secrets at decision time.
- Log redaction for PII/PHI.
- Timeouts (e.g., 10–30 ms sidecar) with safe fallbacks during staged rollout.
Try it free: baseline your site in 60 seconds
Use our Free Website Vulnerability Scanner to spot missing security headers, weak TLS, and common misconfigs before policy rollouts:
- Where to find it: free.pentesttesting.com
- What to expect: an instant summary and downloadable report you can attach to your CI ticket.
Free Website Vulnerability Scanner by Pentest Testing Corp — instant security checks.

Sample security report to check Website Vulnerability, highlighting HSTS and CSP gaps.

Related services & next steps
- At Cyber Rely, we implement and validate policy-as-code pipelines end-to-end—see Web Application Penetration Testing.
- For audit-ready artifacts and sprint-friendly fixes, see Risk Assessment and Remediation Services.
- Keep learning on the Cyber Rely Blog.
Recent Cyber Rely posts you can reference inside your team:
- Prevent Sensitive Data Exposure in React.js — 7 Best Ways
- Best 5 Ways for CSRF Prevention in React.js
- Prevent Directory Traversal Attack in React.js — 7 Best Ways
- npm supply chain attack 2025: ‘Shai-Hulud’ CI fixes
(These are great companions to convert findings into CI checks.)
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about OPA vs Cedar.