5 Blazing Steps to a SEC Item 1.05 Pipeline (Cyber 8-K)
Engineering leaders are now expected to decide fast—and defend later. This guide shows how to ship a developer-friendly SEC Item 1.05 pipeline that automates cyber 8-K automation, materiality assessment, and disclosure evidence collection. You’ll get production-ready code, CI/CD examples, and a signed evidence store pattern—so the decision clock doesn’t beat you.
For a practical PCI DSS 4.0.1 remediation checklist with code (MFA, TLS, secrets, CDE segmentation, CI gates), see PCI DSS 4.0.1 Remediation Patterns.
What we’re building
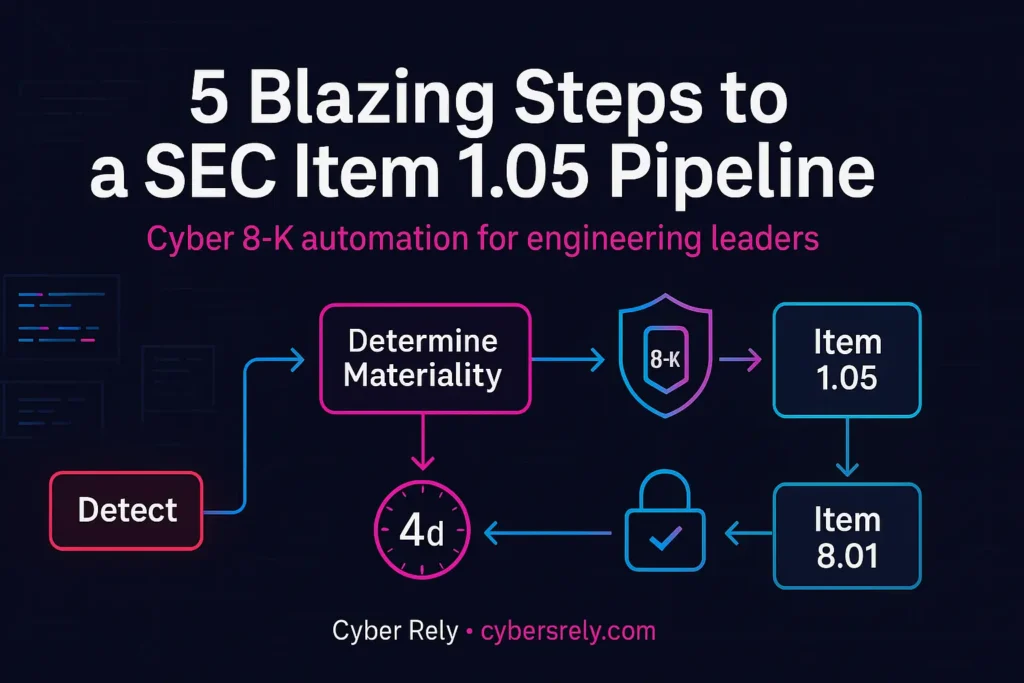
A SEC Item 1.05 pipeline that:
- Models “materiality drivers” in code (systems affected, customer impact, operational disruption, $$ loss).
- Auto-assembles Item 1.05 fact patterns (nature, scope, timing, impact) from logs, tickets, and PRs.
- Tags incidents in CI/CD with severity + probable materiality.
- Packages reproducible evidence to a signed, immutable evidence store.
- Starts four-business-day timers from determination of materiality, and routes non-material events to Item 8.01.
Quick risk snapshot for internet-facing assets? Run our free scanner and attach the result to the case: free.pentesttesting.com.
Step 1 — Model materiality drivers in code
Below is a simple Python domain model to score probable materiality. Adjust thresholds to match your risk appetite.
# materiality.py
from dataclasses import dataclass
from enum import Enum
from typing import List, Dict
class SystemTier(Enum):
TIER_1 = 3 # critical (prod auth, payments, PII lake)
TIER_2 = 2 # important
TIER_3 = 1 # ancillary
@dataclass
class Impact:
customers_affected: int # unique customers/users
revenue_at_risk_usd: float
operational_disruption_hours: float # downtime or severe degradation
data_confidentiality_loss: bool
data_integrity_loss: bool
data_availability_loss: bool
@dataclass
class IncidentContext:
id: str
systems: List[SystemTier]
severity: str # Sev1..Sev4
impact: Impact
regulators_notified: bool = False
MATERIALITY_WEIGHTS: Dict[str, float] = {
"tier": 1.25, "customers": 1.0, "revenue": 1.1, "ops": 0.9,
"c": 0.8, "i": 0.8, "a": 0.8, "sev": 1.2
}
def probable_materiality_score(ctx: IncidentContext) -> float:
tier_score = sum(t.value for t in ctx.systems) * MATERIALITY_WEIGHTS["tier"]
cust_score = min(ctx.impact.customers_affected / 1000, 10) * MATERIALITY_WEIGHTS["customers"]
rev_score = min(ctx.impact.revenue_at_risk_usd / 1_000_000, 10) * MATERIALITY_WEIGHTS["revenue"]
ops_score = min(ctx.impact.operational_disruption_hours / 2, 10) * MATERIALITY_WEIGHTS["ops"]
cia_score = (
(1 if ctx.impact.data_confidentiality_loss else 0) * MATERIALITY_WEIGHTS["c"] +
(1 if ctx.impact.data_integrity_loss else 0) * MATERIALITY_WEIGHTS["i"] +
(1 if ctx.impact.data_availability_loss else 0) * MATERIALITY_WEIGHTS["a"]
)
sev_map = {"Sev1": 4, "Sev2": 2, "Sev3": 1, "Sev4": 0}
sev_score = sev_map.get(ctx.severity, 0) * MATERIALITY_WEIGHTS["sev"]
return round(tier_score + cust_score + rev_score + ops_score + cia_score + sev_score, 2)
def is_probably_material(ctx: IncidentContext) -> bool:
return probable_materiality_score(ctx) >= 10.0 # tune threshold with LegalBonus — Attach an external posture snapshot from our free tool
Free Website Vulnerability Scanner Landing Screenshot

Step 2 — Auto-assemble Item 1.05 fact patterns
Aggregate nature, scope, timing, impact from observability, ticketing, and PR trails.
// fact_pattern.ts (Node 20+)
import { promises as fs } from "fs";
type Evidence = { type: string; path: string; digest?: string; };
type FactPattern = {
incidentId: string;
nature: string; // what happened
scope: string; // what assets/data
timing: string; // discovery + determination timestamps
impact: string; // customers, $$, operations
evidence: Evidence[];
};
export async function buildFactPattern(incidentId: string): Promise<FactPattern> {
const ticket = JSON.parse(await fs.readFile(`./.evidence/${incidentId}/ticket.json`, "utf8"));
const pr = JSON.parse(await fs.readFile(`./.evidence/${incidentId}/pr.json`, "utf8"));
const logs = await fs.readFile(`./.evidence/${incidentId}/alerts.ndjson`, "utf8");
return {
incidentId,
nature: ticket.summary,
scope: `Services: ${ticket.services.join(", ")}; Data: ${ticket.data_involved.join(", ")}`,
timing: `Detected: ${ticket.detected_at}; Determined: ${ticket.materiality_determined_at ?? "TBD"}`,
impact: `Users: ${ticket.users_impacted}; RevRiskUSD: ${ticket.revenue_risk}; OpsHours: ${ticket.ops_hours}`,
evidence: [
{ type: "ticket", path: `ticket.json` },
{ type: "pr", path: `pr.json` },
{ type: "alerts", path: `alerts.ndjson` }
]
};
}Tip: When your IR lead clicks “Material” in the ticket, stamp materiality_determined_at—that’s the legal start for the four-business-day timer.
Step 3 — CI/CD: tag incidents & package evidence (to a signed store)
A GitHub Actions workflow that routes to Item 1.05 vs Item 8.01, signs artifacts, and publishes to an immutable bucket.
# .github/workflows/incident-evidence.yml
name: Incident Evidence Package
on:
workflow_dispatch:
inputs:
incident_id:
description: "Incident ID"
required: true
push:
paths:
- ".evidence/**"
jobs:
package:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Set up Python
uses: actions/setup-python@v5
with: { python-version: "3.11" }
- name: Compute probable materiality
run: |
pip install orjson
python - <<'PY'
import json, sys, orjson, pathlib
from materiality import IncidentContext, Impact, SystemTier, is_probably_material
iid = "${{ github.event.inputs.incident_id || 'latest' }}"
ticket = orjson.loads(pathlib.Path(f".evidence/{iid}/ticket.json").read_bytes())
ctx = IncidentContext(
id=iid,
systems=[SystemTier[s] for s in ticket["systems"]],
severity=ticket["severity"],
impact=Impact(
customers_affected=ticket["users_impacted"],
revenue_at_risk_usd=ticket["revenue_risk"],
operational_disruption_hours=ticket["ops_hours"],
data_confidentiality_loss=ticket["c_loss"],
data_integrity_loss=ticket["i_loss"],
data_availability_loss=ticket["a_loss"]
)
)
print("probable_material:", "true" if is_probably_material(ctx) else "false")
PY
- name: Create reproducible tarball
run: |
mkdir -p dist
tar --sort=name --mtime='UTC 2024-01-01' --owner=0 --group=0 \
-czf dist/evidence.tar.gz .evidence/${{ github.event.inputs.incident_id }}
- name: Sign package (Sigstore/cosign or in-toto)
run: |
echo "$SIGNING_KEY" | base64 -d > key.pem
openssl dgst -sha256 -sign key.pem -out dist/evidence.tar.gz.sig dist/evidence.tar.gz
env:
SIGNING_KEY: ${{ secrets.SIGNING_KEY_BASE64 }}
- name: Upload to immutable bucket
run: |
aws s3 cp dist/evidence.tar.gz s3://evidence-store/${{ github.event.inputs.incident_id }}/ --sse AES256
aws s3 cp dist/evidence.tar.gz.sig s3://evidence-store/${{ github.event.inputs.incident_id }}/ --sse AES256
- name: Decide disclosure path
id: route
run: |
MATERIALITY=$(gh run view ${{ github.run_id }} --log | grep probable_material | tail -1 | awk '{print $2}')
if [ "$MATERIALITY" = "true" ]; then
echo "route=item1_05" >> $GITHUB_OUTPUT
else
echo "route=item8_01" >> $GITHUB_OUTPUT
fi
- name: Post status
run: echo "Routed to ${{ steps.route.outputs.route }}"
# next: call your disclosure bot, or open a prefilled doc for LegalImmutable evidence store (Terraform, AWS S3 with Object Lock + versioning):
# evidence_store.tf
resource "aws_s3_bucket" "evidence" {
bucket = "evidence-store"
object_lock_enabled = true
}
resource "aws_s3_bucket_versioning" "evidence" {
bucket = aws_s3_bucket.evidence.id
versioning_configuration { status = "Enabled" }
}
resource "aws_s3_bucket_server_side_encryption_configuration" "evidence" {
bucket = aws_s3_bucket.evidence.id
rule { apply_server_side_encryption_by_default { sse_algorithm = "AES256" } }
}
resource "aws_s3_bucket_object_lock_configuration" "evidence" {
bucket = aws_s3_bucket.evidence.id
rule {
default_retention {
mode = "GOVERNANCE" # prevent deletion/shortening without elevate
days = 365
}
}
}Step 4 — Start the four-business-day timer from determination
The clock starts when you determine materiality, not when you detect the incident. Here’s a simple scheduler that respects business days (no holidays handling shown; plug your calendar later).
# timer.py
from datetime import datetime, timedelta
def add_business_days(start: datetime, days: int) -> datetime:
d = start
added = 0
while added < days:
d += timedelta(days=1)
if d.weekday() < 5: # Mon-Fri
added += 1
return d
def item_105_deadline(determined_at_iso: str) -> str:
start = datetime.fromisoformat(determined_at_iso)
deadline = add_business_days(start, 4)
return deadline.isoformat()
print(item_105_deadline("2025-10-23T11:30:00"))Wire this into your ticket UI so Legal sees a live countdown.
Step 5 — Route Item 1.05 vs Item 8.01 with guardrails
// route.ts
import { buildFactPattern } from "./fact_pattern.js";
import { execSync } from "node:child_process";
export async function routeDisclosure(incidentId: string, material: boolean) {
const fp = await buildFactPattern(incidentId);
if (material) {
// Prepare Item 1.05 disclosure package
execSync(`gh issue comment ${incidentId} --body "Routed to Item 1.05. Evidence: evidence.tar.gz (signed). Timing: ${fp.timing}"`);
// trigger 8-K drafting workflow, notify Legal
} else {
execSync(`gh issue comment ${incidentId} --body "Routed to Item 8.01 (not material). Evidence retained. Timing: ${fp.timing}"`);
// optional: prepare 8-K Item 8.01 or internal comms only
}
}Sample Report Screenshot by the tool to check Website Vulnerability

Run it here: free.pentesttesting.com (light scan, instant results).
When to call in specialists
If your assessment shows likely materiality—or you need a defensible control map before the next exam—loop in our teams:
- Risk Assessment Services (gap analysis, roadmap, audit-ready artifacts).
- Remediation Services (close gaps fast; evidence-backed fixes).
Further dev reading on our blog
Keep your engineers sharp with practical posts from the Cyber Rely Blog:
- 7 Proven Defenses for the Pixnapping Android Exploit (dev-focused mitigation playbook).
- Best 7 Ways to Prevent LDAP Injection in React.js (with code).
- Best 7 Ways to Check for Subdomain Takeover in React.js.
- Fix Weak SSL/TLS Configuration in TypeScript (hands-on hardening).
Implementation checklist (copy/paste for your backlog)
- Add materiality drivers module + tests.
- Stamp
materiality_determined_atin tickets; show Item 1.05 countdown. - CI job: build reproducible tar of
.evidence/INCIDENT_ID/**and sign. - Immutable evidence store with versioning + governance retention.
- Router: Item 1.05 vs Item 8.01 with Legal notification + templates.
- Attach external scan result (JSON/PDF) from the free tool.
Final CTAs
- Bookmark the Cyber Rely Blog for developer-grade security content.
- Run a quick internet-facing risk snapshot with our free scanner.
- Need an audit-ready path? Explore Risk Assessment and Remediation services.
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about SEC Item 1.05 Pipeline (Cyber 8-K).