10 Best Ways to Prevent XML Injection in React.js
XML Injection in React.js is a sneaky class of bugs that shows up when apps parse or render untrusted XML—often from integrations (payment gateways, feeds, SSO metadata), file uploads, or rich-text imports. While React escapes text by default, developers can still introduce injection risks via unsafe parsing, rendering, or serialization flows. In this guide, we’ll break down how XML Injection happens, how to detect it, and how to fix it with practical, copy-pasteable code.

We’ll also link to related resources—like our post on Broken Authentication in WordPress—and previous React security articles, plus include backlinks to our service pages so you can take action today.
What is XML Injection in React.js?
XML Injection occurs when untrusted XML is accepted and then:
- parsed in the browser (e.g.,
DOMParser, third-party libs), - rendered into the DOM (e.g.,
dangerouslySetInnerHTML), or - forwarded to an API without validation, enabling attacks such as entity expansion (“Billion Laughs”), data tampering, or stepping stones to XSS and backend XXE.
Key idea: treat XML like executable input. Parse it safely, validate shape and size, never inject it directly into the DOM, and never trust it blindly on the server.
How XML Injection in React.js Happens (Common Pitfalls)
1) Parsing untrusted XML with DOMParser and rendering it
// ❌ Insecure example: Parses attacker XML and renders it as HTML/XML
const InsecureXmlViewer: React.FC<{ xmlText: string }> = ({ xmlText }) => {
const doc = new DOMParser().parseFromString(xmlText, "application/xml");
const asString = new XMLSerializer().serializeToString(doc);
// If asString contains malicious nodes or crafted markup,
// this can be dangerous when rendered as HTML:
return <div dangerouslySetInnerHTML={{ __html: asString }} />;
};2) Trusting third-party XML without size/shape limits
Even if you don’t show it in the UI, passing unbounded XML to other components or to APIs can cause denial-of-service (entity expansion) or unexpected behavior downstream.
3) “Just convert to HTML” patterns
Converting XML to HTML to “nicely display it” often ends with dangerouslySetInnerHTML, opening the door to DOM clobbering or script gadget abuse.
Secure Parsing: Safer Patterns for XML in React
Use a data-first approach: parse to a plain JS object with a hard-ening parser, validate the shape, then render with React as data (not markup).
✅ Example: Parse with fast-xml-parser and validate with Zod
// npm i fast-xml-parser zod dompurify
import React from "react";
import { XMLParser } from "fast-xml-parser";
import { z } from "zod";
import DOMPurify from "dompurify";
const xmlSchema = z.object({
feed: z.object({
item: z
.array(
z.object({
title: z.string().max(200),
link: z.string().url().optional(),
summary: z.string().max(1000).optional()
})
)
.nonempty("Feed must contain at least one item")
})
});
const parser = new XMLParser({
ignoreAttributes: false,
// fast-xml-parser doesn't process external entities; we still:
processEntities: false,
// Safe conversions
parseTagValue: true,
trimValues: true,
});
type FeedItem = z.infer<typeof xmlSchema>["feed"]["item"][number];
export const SafeXmlFeed: React.FC<{ xmlText: string }> = ({ xmlText }) => {
// 1) Guard size to mitigate large payloads / "billion laughs"-style abuse
if (xmlText.length > 200_000) {
return <p>XML too large. Please upload a smaller file.</p>;
}
// 2) Basic “no DTD” heuristic (defense in depth)
if (/\<\!DOCTYPE/i.test(xmlText)) {
return <p>DTD not allowed in this XML.</p>;
}
// 3) Parse as data, not markup
const json = parser.parse(xmlText);
// 4) Validate expected shape
const parsed = xmlSchema.safeParse(json);
if (!parsed.success) {
return <pre>Invalid XML structure: {parsed.error.message}</pre>;
}
const items: FeedItem[] = parsed.data.feed.item.slice(0, 50); // limit
return (
<ul className="list-disc pl-5">
{items.map((it, i) => (
<li key={i}>
<strong>{DOMPurify.sanitize(it.title)}</strong>
{it.link && (
<>
{" — "}
<a href={it.link} rel="noopener noreferrer">
{DOMPurify.sanitize(it.link)}
</a>
</>
)}
{it.summary && <p>{DOMPurify.sanitize(it.summary)}</p>}
</li>
))}
</ul>
);
};Why does this help for XML Injection:
- We parse to data (JSON) and never render the raw XML as HTML.
- We limit size, forbid DTD hints, and validate shape.
- We sanitize any strings we do display (defense in depth).
📷 Screenshot of the free Website Vulnerability Scanner Tools page

Blocking Dangerous UI Patterns
Avoid dangerouslySetInnerHTML for XML
If you must render formatted content, whitelist and transform nodes—don’t dump raw XML/HTML. Render safe React components from parsed data instead.
// ✅ Render a whitelisted subset of nodes explicitly
type Node = { type: "p" | "code"; text: string };
const WhitelistRenderer: React.FC<{ nodes: Node[] }> = ({ nodes }) => (
<div>
{nodes.map((n, i) =>
n.type === "p" ? (
<p key={i}>{n.text}</p>
) : (
<pre key={i}>{n.text}</pre>
)
)}
</div>
);End-to-End Defense: Frontend + API
Even with a safe React layer, you should re-validate on the server. Many attacks attributed to XML Injection in React.js actually detonate on the backend (e.g., unsafe XML parsers, XXE).
Node/Express: Accept XML safely and convert to JSON
// server.ts
// npm i express fast-xml-parser helmet zod
import express from "express";
import helmet from "helmet";
import { XMLParser } from "fast-xml-parser";
import { z } from "zod";
const app = express();
// Only accept text; do manual limits instead of auto-parsing XML via body parsers
app.use(helmet({
contentSecurityPolicy: false // enable CSP separately for the frontend build
}));
app.post("/upload-xml", express.text({ type: ["application/xml", "text/xml"], limit: "200kb" }), (req, res) => {
const xmlText = req.body || "";
if (/\<\!DOCTYPE/i.test(xmlText)) {
return res.status(400).json({ error: "DTD not allowed" });
}
const parser = new XMLParser({ processEntities: false, ignoreAttributes: false });
let data: unknown;
try {
data = parser.parse(xmlText);
} catch {
return res.status(400).json({ error: "Invalid XML" });
}
const schema = z.object({
feed: z.object({
item: z.array(z.object({
title: z.string().max(200),
link: z.string().url().optional(),
summary: z.string().max(1000).optional()
})).max(100) // apply server-side cap as well
})
});
const result = schema.safeParse(data);
if (!result.success) {
return res.status(400).json({ error: "Bad shape", detail: result.error.issues });
}
// Safe to use data downstream
return res.json({ ok: true, count: result.data.feed.item.length });
});
app.listen(3000, () => console.log("API on http://localhost:3000"));Add CSP in your React deployment
CSP won’t “fix” XML Injection Vulnerability, but it reduces XSS blast-radius.
# Example HTTP headers from your CDN or reverse proxy
Content-Security-Policy: default-src 'self'; script-src 'self'; object-src 'none'; base-uri 'self'; frame-ancestors 'self';
X-Content-Type-Options: nosniff
Referrer-Policy: strict-origin-when-cross-originRed-Team Your App: Testing XML Injection in React.js
Create tests that simulate malicious payloads frequently seen in XML Injection scenarios.
// xml.test.ts
import { XMLParser } from "fast-xml-parser";
const parser = new XMLParser({ processEntities: false });
test("rejects DTD-like payloads", () => {
const xml = `<!DOCTYPE lolz [ <!ENTITY lol "lol"> ]><feed><item><title>&lol;</title></item></feed>`;
// Basic DTD check before parsing (recommended)
expect(/\<\!DOCTYPE/i.test(xml)).toBe(true);
});
test("parses simple feed safely", () => {
const xml = `<feed><item><title>Hello</title></item></feed>`;
const obj = parser.parse(xml);
expect(obj.feed.item[0].title).toBe("Hello");
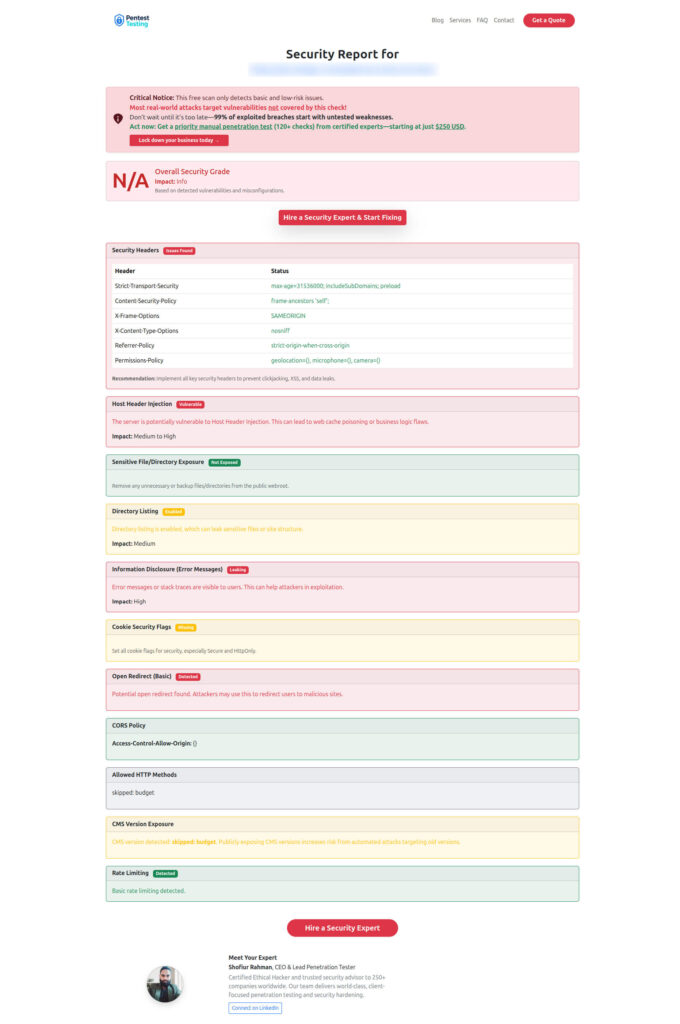
});📷 Sample Assessment report generated by our tool to
Real-World Checklist to Prevent XML Injection in React.js
- Never render raw XML. Convert to data (JS objects) and render components.
- Disallow DTD/Entities. Quick string check + parser settings.
- Limit size and depth to mitigate expansion and DoS.
- Validate schema with Zod or similar both client and server.
- Sanitize displayed strings, even when rendering from data.
- Set CSP on production.
- Re-validate on the server; don’t rely on client checks.
- Audit third-party libraries handling XML.
- Log and monitor XML parsing errors centrally.
- Automate tests for malicious XML payloads.
The phrase XML Injection should now feel familiar—these practices make it a non-event.
More Code Patterns
Stream-parse on the server (protects memory)
// Using a SAX-style parser (pseudo-code)
import sax from "sax";
const strict = true;
const parser = sax.parser(strict, { lowercase: true });
parser.onerror = () => { /* reject request */ };
parser.ondoctype = () => { /* reject immediately */ };
parser.ontext = (t) => { /* accumulate with limits */ };
parser.onopentag = (node) => { /* enforce whitelist */ };
// Pipe request body to parser with size caps from your reverse proxy.Convert XML ➜ data ➜ render UI (no innerHTML)
type Product = { id: string; name: string; price: number };
const ProductList: React.FC<{ products: Product[] }> = ({ products }) => (
<table>
<thead><tr><th>ID</th><th>Name</th><th>Price</th></tr></thead>
<tbody>
{products.map(p => (
<tr key={p.id}><td>{p.id}</td><td>{p.name}</td><td>{p.price}</td></tr>
))}
</tbody>
</table>
);Related Reading & Previous Posts
- Deep-dive WordPress issue: Broken Authentication in WordPress
- Previous Cybersrely guides:
These posts complement the present article on XML Injection with front-end performance and security patterns.
Services & Backlinks (Take Action)
Managed IT Services
Gain resilience, observability, and secure baselines across your stack. → Pentest Testing Corp – Managed IT Services
AI Application Cybersecurity
Threat-model LLM features, secure prompt flows, and guardrails. → AI Application Cybersecurity
Offer Cybersecurity to Your Clients
White-label assessments and pentests to expand your agency’s scope. → Offer Cybersecurity Service to Your Client
Talk to Us
Have an XML upload or feed integration to review? → Contact Cybersrely
These service links are included to strengthen the relevance and help you remediate XML Injection in React.js quickly.
Quick “Copy & Paste” Snippets You Can Use Today
Client guard for paste/upload:
const tooBig = (s: string) => s.length > 200_000 || (s.match(/\</g) || []).length > 100_000;DTD block before parse:
if (/\<\!DOCTYPE/i.test(xml)) throw new Error("DTD not allowed");Type-safe mapping after parse:
type Feed = { feed: { item: Array<{ title: string; link?: string; summary?: string }> } };
function asFeed(x: unknown): Feed {
// minimal runtime validation if schema libs not available
if (!x || typeof x !== "object" || !("feed" in x)) throw new Error("Bad feed");
return x as Feed;
}These little guards close most holes contributing to XML Injection in React.js.
Conclusion
When teams say “React escaped it, so we’re safe,” they often miss parser and rendering anti-patterns that enable XML Injection. The fix is simple: treat XML as data, parse safely, validate shape, and render with components—not with raw markup. Add server-side checks and observability, and you’ve eliminated an entire class of client-to-server issues.
If you’d like a quick review of your XML flows or a secure import wizard, reach out via our Contact page—we can help you close XML Injection in React.js gaps fast.
P.S. If you enjoyed this, see our related posts above—and run a quick scan using our free tool at https://free.pentesttesting.com/ to catch misconfigurations that pair dangerously with XML Injection Issues.
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about XML Injection in React.js.